Protected application can log important events to a text file.
Select "Enable logging" option to enable logging for protected application.
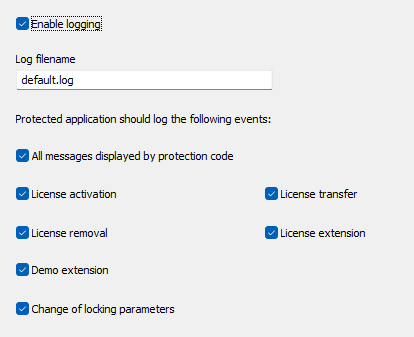
Protected application can log the following information:
- All messages displayed by protection code to end user (errors, notifications...)
- License activation: site code, mid code, activation code, serial number (if applicable).
- License removal: removal code
- License transfer: new site code, new activation code
- License extension: site code, mid code, activation code
- Demo extension: site code, mid code, activation code
- Change of locking parameter: parameter name, old hash value, new hash value
Log filename
Default log filename is "default.log" and it can be changed here. This filename is embedded into protected application during protection process.
By default, log file is located in license directory on remote machine.
CSIDL_COMMON_APPDATA\<license dir>
Where <license dir> is the name of directory with license file (available in protection report)
Folder identified by CSIDL_COMMON_APPDATA it the file system directory that contains application data for all users.
A typical path is:
Windows 7:
C:\ProgramData\<license dir>
C:\Documents and Settings\All Users\Application Data\<license dir>
Windows 10:
C:\Users\All users\<license dir>
Log file structure
Each log file entry contains:
- date and time (in DD.MM.YYYY HH:MM format)
- full path to protected application which generated entry (log file may be shared by multiple protected applications).
- event message